Building a Solution to Today's Problem: Mobile Device Application Overload
By: Lee Reiber, Vice President of Mobile Forensic Solutions at AccessData
Crime today is no longer confined to the streets. Crimes are increasingly committed in a cyber-world. Looking back, I recalled patrolling the streets as a young officer in a Pacific Northwest city, and responding to calls for service involving domestic disturbance, burglary, robbery, grand theft, battery, and homicide. Officers receiving calls from dispatch via radio eventually transitioned to officers receiving information on mobile data terminals (MDT). We arrived on scene, did the best we could to resolve the situation, and left; later documenting the event by pen. During these calls for service, we could really see the situation for what it was. There was no Facebook, Instagram, Twitter, Ask, Secret or any other social media. The event occurred in real time. Cyber bullying, cyber stalking, and any other cyber related crimes were not part of the equation. Cybercrimes, at that time, were chalked up to the darkest form of crime, the online sexual exploitation of children. When I transitioned to the computer crimes task force, I saw first-hand how this heinous crime had no boundaries or limits. It lived in a space that was un-policed, without jurisdiction and honestly infinite. It was at that time I realized that crime would, one day, move from the streets to the realm of the digital environment; an environment with infinite possibilities and no discernible edges.
Fast forward to today. Law enforcement has a better grasp of the fact that digital evidence exists for almost every crime imaginable. However, law enforcement does not have a grasp on the “mobility” shift; the world of the mobile device application or app, and the likelihood of evidence being contained within an application’s data on a mobile device.
Currently, 91% of people worldwide use some sort of mobile device, and 82% of mobile media time is spent via an application. There are over 800,000 applications available from the Apple Store, and over 800,000 applications available from the Google Play Store. Over 16 billion photos alone have been shared via Instagram. There are over 1 billion active Facebook users worldwide. Over 200,000 Google searches are conducted every minute of every day and over 600,000 emails are sent every minute of every day. These statistics are staggering. Data from these mobile applications are stored in that application’s SQL database, located on the mobile device. Considering that a crime can be facilitated, or committed via a mobile device or mobile application, it is imperative that law enforcement be able to quickly adapt to the ever evolving world of mobile applications and mobile forensics. Access Data’s Mobile Phone Examiner Plus (MPE+) provides law enforcement with that ability through the SQL Builder.
The MPE+ SQL Builder is not an add-on tool, but a feature built into AccessData's Mobile Phone Examiner Plus (MPE+). This feature allows the user to build custom queries simply by selecting the SQL database, the relevant table or tables, and the associated rows containing the data. These queries can be built as soon as an application is available. Users of MPE+ do not need to wait for a software upgrade to be able to process the new application’s data. Once the query is built, a user simply executes the query and the data is pulled from the database into the interface. This data can then be published into the MPE+ interface and can be immediately reported on. This feature makes every app database open for investigation and the hidden data types exposed. All other mobile forensic solutions have a limited number of applications they support but they only allow users to visualize that data. Therefore, extracting the data with these other solutions is cumbersome and difficult. With MPE+ SQL Builder, users simply create their own queries and execute on ANY and ALL applications. In essence, all applications utilizing a SQL Database are supported by MPE+. What is even better, the user can also save those queries for later use, or share them with other MPE+ users!
For example, a KiK Messenger can be used as a form of communication. KiK is one of many popular communication software apps available to both Android and iOS. When over 70% of communication is via apps and not built in messaging like SMS and MMS, it is important that users can extract the data they are seeking. Using the MPE+ SQL Builder a user simply right clicks on the database file, kik.sqlite and selects SQL Builder (Figure 1).
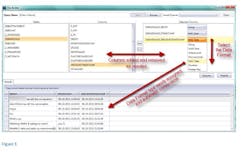
The SQL Builder then opens showing the various tables within the database. (Figure 2) The ZKIKMESSAGE Table is selected and the rows are shown in the adjacent column.
Once the rows are selected, users can add or remove a row using the navigational arrows between columns. Users can also assign the appropriate data type to the selected row. This is critical since the data types can vary between applications. Once the data type is assigned, users can execute the query to display the parsed data below. This query can be saved for later use by selecting the Save button. (Figure 3)
After the data is displayed, users can still change the data type if needed and press “execute” again. This is important since Android can have numerous date and time formats. Once the data executed is complete users can publish the results to the MPE+ interface to be included in the AD1 forensic image as well as the report. (Figure 4)
Today, criminals are assisted in the commission of their crimes by the mobile devices and applications they use. Application evidence is critical in any and all investigations. By allowing the user to pull this important and volatile data from any SQL database, AccessData's MPE+ has given the upper hand to the law enforcement investigator. Using MPE+ SQL Builder, the relevant evidence can be extracted and a criminal's intentions exposed.
Staying ahead of the app, MPE+ is changing the way mobile forensics is done by introducing an entirely different approach to mobile device forensics.