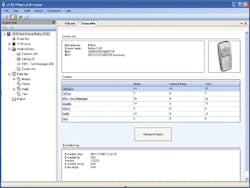
CelleBrite Ltd.'s UFED Physical Pro expands on the already robust logical extraction feature set found in the UFED to add the capability to extract deleted data and user passwords located in phone memory. The UFED Physical Pro's capability to provide deeper, more invasive access to mobile phone memory is the latest innovation for CelleBrite's UFED system currently in use by law enforcement and security agencies worldwide. With an add-on module that can be deployed to any UFED device, existing UFED user can easily upgrade their systems with this latest functionality. Utilizing CelleBrite UFED's user friendly and field-proven user interface, a complete high-speed hex dump of the phone memory is acquired without the need of cumbersome PC drivers. The flash memory of the phone is imaged as a binary file, which is decoded with the Physical Analyzer PC software tool. Critical data such as user lock codes and deleted information such as text messages, call history, pictures, and video are retrieved, sorted and decoded by CelleBrite's Physical Pro engine. The UFED Physical Analyzer also includes robust search tools for manual hex dump analysis, as well as an expert mode which allows advanced capabilities for researchers. Extracted data is presented in clear concise reports which can be used for intelligence gathering, investigative research, and legal evidence in court.
Features include:
- Access to deleted data (ex: deleted call history, text messages, pictures, phonebook entries and videos)
- On board password extraction with no PC required for field use (450+ models)
- Open Source Plug-In support: author, collaborate on, and utilize custom search and value parsing algorithms
- Intelligent string finder
- Built-in knowledge-base of each phone's memory structure for automated retrieval, decoding and translation of critical data
- Hierarchical "tree" view for efficient and fast navigation
- Advanced search capabilities both to novice and expert users
- Customizable search, parsing and report functions
- Proprietary, forensically sound bootloaders for most supported devices
- Deep access to data inaccessible by logical methods
- Handset security or PIN lock code
- Access to deep internal memory
- Phone internal data (ex. IMSI history, past SIM cards used, past user lock code history where supported)