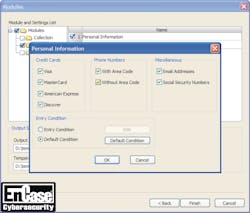
With the explosion of the digital world, organizations store their data in electronic format – from source code, stock trade transactions, and confidential emails to credit card data, personally identifiable information (PII) and HR data. Guidance Software’s EnCase Cybersecurity is designed for the information security, network defense and incident response teams that are tasked with protecting this information, and identifying and responding to network threats.
EnCase Cybersecurity features profiling and whitelisting capabilities that allow organizations that have identified suspicious behavior to zero in on the offending malware, which is often designed to evade end-point and perimeter detection defenses. Once the malware is discovered, EnCase Cybersecurity can detect file similarities between suspicious executables, allowing an organization to expose other iterations of the threat as is often required when dealing with polymorphic malware. Once the malware is located, EnCase Cybersecurity also kills running processes, wipes malware artifacts from the disk and resets registry keys, allowing for full recovery without taking machines offline.
EnCase Cybersecurity complements and augments existing information security tools that aim either to block or quarantine data - such as firewalls, intrusion prevention systems, antivirus, or data loss prevention tools - or that trigger or correlate alerts, such as intrusion detection systems, configuration management, or SIM and SIEM tools.

![Let 01 Cover0920 Digital Edition 5f4daeb1086a7[1] Let 01 Cover0920 Digital Edition 5f4daeb1086a7[1]](https://img.officer.com/files/base/cygnus/ofcr/image/2020/09/LET_01_Cover0920Digital_edition.5f4daeb1086a7_1_.5f5b81a5e15cd.png?auto=format,compress&fit=crop&q=45&h=139&height=139&w=250&width=250)


